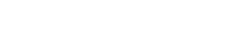How hackers are the use of electronic mail to unfold phishing assaults
The document notes that the primary electronic mail won via the sufferers arrives in standard model, by way of a notification at once from Google. This is since the hacker shared the gathering with the top person. The electronic mail comes from a [email protected] cope with. That cope with is professional and can also be identified via hackers and end-users alike. Users may additionally generally tend to click on at the hyperlink as soaring over the URL will display a sound Google hyperlink. Furthermore, the emails also are redirecting customers to a sound Google web page.
Google Collections paintings with a number of other card-like figures. Users too can hyperlink to photographs, webpages, and so forth inside of that assortment. However, clicking at the card is appearing a suspicious hyperlink and message. The hackers need their sufferers to go into this hyperlink which seems like a Google shape. Clicking this may occasionally redirect customers to a pretend cryptocurrency website online, which is able to in the end scouse borrow cash.
How to spot such an electronic mail
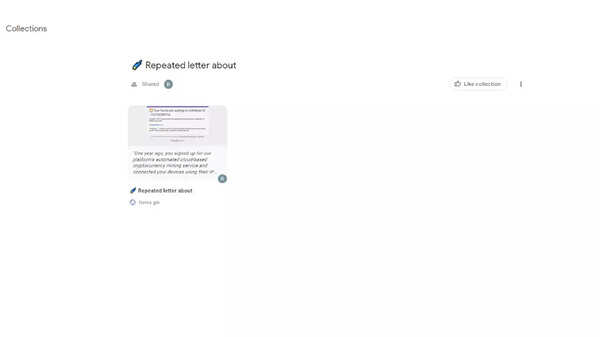
As proven within the pictures above, the ground of the Google web page tells a very powerful difference: “This content is neither created nor endorsed by Google.” Like many different websites, Google additionally permits customers to place any content material on their web page and hackers are abusing this privilege via striking illegitimate, malicious websites.
The document additionally notes that hackers are nesting the malicious hyperlinks to make certain that their payloads achieve their goal. For this, attackers are hiding those hyperlinks within the 3rd phase. Seeing the Google hyperlinks person would possibly get started trusting the hyperlinks and hackers are leveraging this not unusual self assurance amongst customers.